Reviews of the top-rated ZTNA (Zero Trust Network Access) providers, comparing their strengths in security features, scalability, deployment options, and integration capabilities, with a focus on solutions from Palo Alto, Akamai, Zscaler, and others, emphasising their suitability for various organisational needs. |
The top rated ZTNA vendors are Palo Alto, Akamai, Zscaler, Perimeter 81, Cato Networks, Cloudflare, Fortinet, Forcepoint, Check Point and Cisco. When comparing ZTNA vendors, you should consider data loss, threat protection, agentless deployment, reporting and SASE offerings.
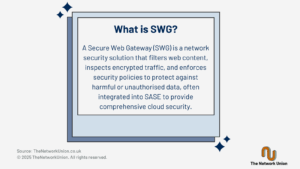
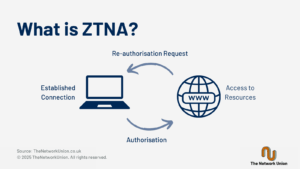
What is ZTNA (Zero Trust Network Access)?
Zero Trust is about adding an additional layer of security. It means not fully trusting anything or anyone by default, and instead assuming that everything should be verified before being given access to a resource.
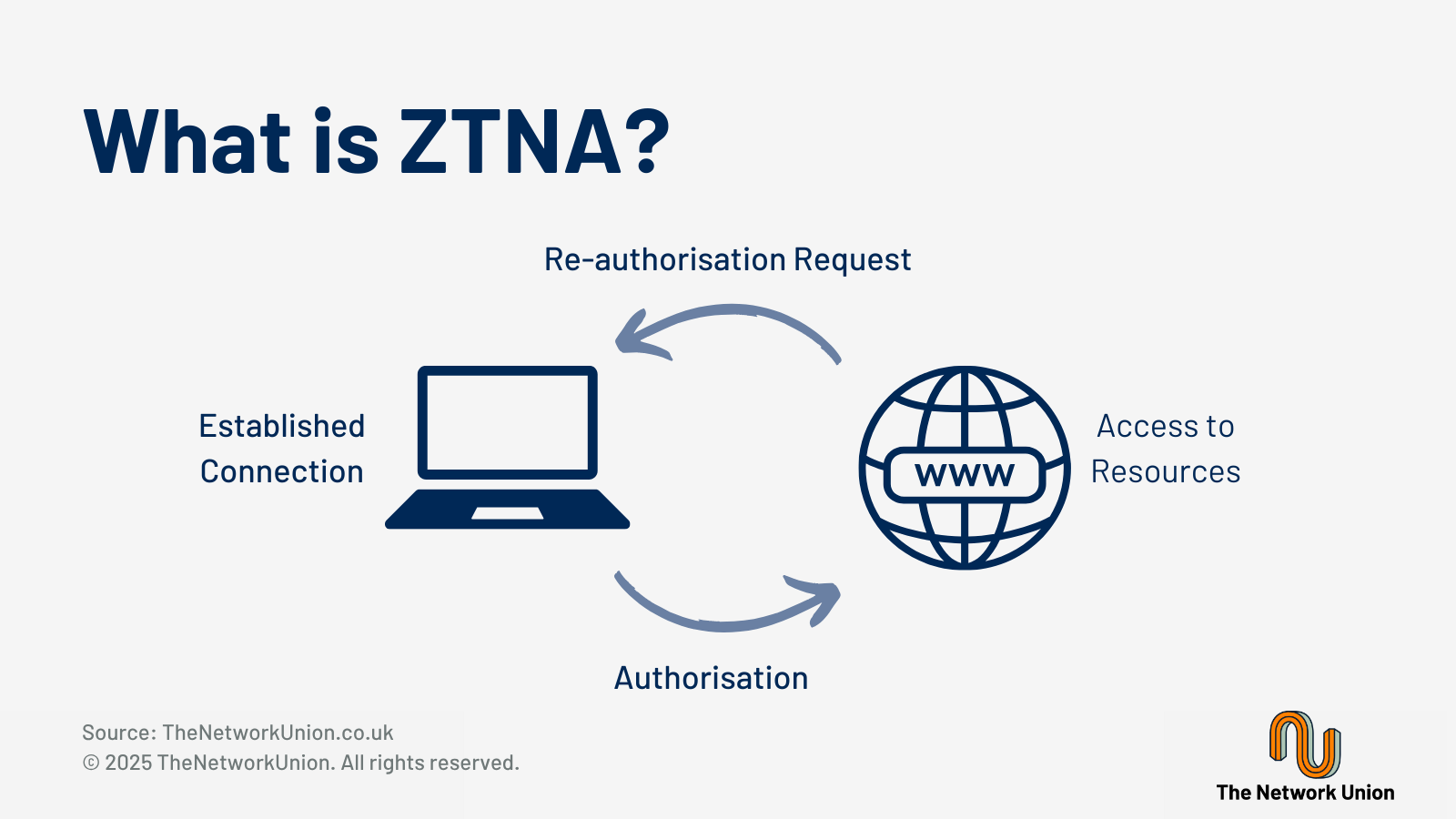
Enterprises are rethinking the access model for users and applications, ensuring that their business is safe from today’s threats while still providing seamless and reliable access from anywhere. This is where Zero Trust Network Access (ZTNA) comes in. ZTNA is a security model designed to replace legacy models which made the assumption that anything inside a network was safe. This allowed bad actors to have free rein over data and infrastructure on the network should they gain access. Zero Trust intends to limit these issues with granular security steps throughout a network infrastructure. A complete Zero Trust implementation covers network infrastructure, users, workloads and applications. Choosing the right approach to Zero Trust for your company starts with choosing the right vendor. All vendors offer solutions designed specifically for their target demographic, so it is imperative to know which is the best option for each organisation’s path to Zero Trust.
Questions to help shortlist Zero Trust providers and vendors
- Is each request verified on a case-by-case basis? If so, how does this work?
- Does the vendor’s solution work with existing identity providers and Multi-Factor Authentication (MFA) solutions?
- Does the solution use artificial intelligence and/or machine learning to predict potential bad actors or behavioural actions?
- Can the vendor’s solution be managed from a single portal? Is it hosted in-cloud, on-premises or both?
- Does the solution integrate with Security Information and Event Management (SIEM) providers?
- Does the vendor’s solution support Single Sign-On (SSO) across all devices, users, departments and geographic locations using an open standard like Security Assertion Markup Language (SAML)?
- Is the vendor’s solution preventative or for visibility only? Can defensive actions be automated?
- What support model does the vendor offer? Is it included in subscription fees? Do they recommend professional services?
- What is the user experience like? Is it simple to implement and operate for users and administrators of all backgrounds?
- What level of visibility is provided by the vendor’s logs and context? Do they have logging APIs or syslog integration?
- What options are provided for integrations into the broader cybersecurity ecosystem?
What is the Palo Alto ZTNA solution?
Palo Alto is a well-known industry leader with a broad product base. They are a good choice for large enterprises that have a need for a diverse mix of on-premise and SaaS requirements. Palo Alto also offers developing technologies such as DNS Security, which uses Machine Learning and Artificial Intelligence (AI)-supported URL filtering to detect and prevent zero-day web attacks.
What are the pros and cons of Palo Alto ZTNA?
Palo Alto ZTNA Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 22/10/2024 02:55 PM | hyelland | 22/10/2024 02:55 PM | ✓ Palo Alto’s solution is comprehensive and includes SaaS Security, Advanced URL Filtering, DNS Security, Cloud Identity Engine and Firewalls powered by Machine Learning that cover all firewall implementation types (including hardware, software and cloud | ❌ There have been some mobile endpoint and agent update issues, and according to confirmed customer feedback, their support model often doesn’t meet customer expectations. |
| 2 | hyelland | 22/10/2024 02:55 PM | hyelland | 22/10/2024 02:55 PM | ✓ They are also known for offering a bleeding-edge Cloud Access Security Broker (CASB) that extends the Zero Trust model to SaaS applications. Palo Alto’s Cloud Identity Engine (ICIE) is also an intuitive approach to identity management. | ❌ Palo Alto offers Panorama for centralised management, but the customer is responsible for deployment and hosting. Some organisations may prefer this model, but many others would choose a vendor-hosted management portal which many of Palo Alto’s competi |
| 3 | hyelland | 22/10/2024 02:55 PM | hyelland | 22/10/2024 02:55 PM | ❌ The solution’s compatibility with Azure lacks an SD-WAN hub integration. | |
| 4 | hyelland | 22/10/2024 02:55 PM | hyelland | 22/10/2024 02:55 PM | ❌ High Cost | |
| 5 | hyelland | 22/10/2024 02:55 PM | hyelland | 22/10/2024 02:55 PM | ❌ Complexity of design can be an issue due to multiple product offerings required by a new organisation to achieve a comprehensive solution on the Palo Alto platform. | |
| Pros | Cons |
What is the Akamai ZTNA solution?
Akamai is a leader in Zero Trust platforms with extensive experience in high-performance global content delivery, setting them apart from competitors. The company is a good choice for enterprises that host large amounts of sensitive data that has to be accessible 100% of the time from anywhere for customers and employees. Akamai provides excellent protection from downtime and known attacks.
What are the pros and cons of Akamai ZTNA?
Akamai ZTNA Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 22/10/2024 02:47 PM | hyelland | 22/10/2024 02:47 PM | ✓ Akamai’s solution is noted to be simple to deploy, with the ability to sit outside of organisational firewall(s). | ❌ The completion and execution of Akamai’s roadmap items leaves areas of improvement for features desired by their customers. |
| 2 | hyelland | 22/10/2024 02:47 PM | hyelland | 22/10/2024 02:47 PM | ✓ User interfaces are intuitive and easy to use and manage for end-users. | ❌ While the focus on prevention of ransomware is seen as a positive, in total, the hyper-focus detracts from other useful security features like intelligent application execution controls. |
| 3 | hyelland | 22/10/2024 02:47 PM | hyelland | 22/10/2024 02:47 PM | ✓ Akamai has DDoS prevention features that go beyond industry standards, along with network security, workload security and additional APIs for integration and automation. | |
| 4 | hyelland | 22/10/2024 02:47 PM | hyelland | 22/10/2024 02:47 PM | ✓ High user confidence due to Akamai’s Intelligent Edge Platform, which operates with 100% SLA and manages up to 30% of all web traffic globally. | |
| 5 | hyelland | 22/10/2024 02:47 PM | hyelland | 22/10/2024 02:47 PM | ✓ Another key feature offered by the Akamai solution is cloud-based management, which is completely accessible by API with logs that can be exported directly to SIEM products. | |
| Pros | Cons |
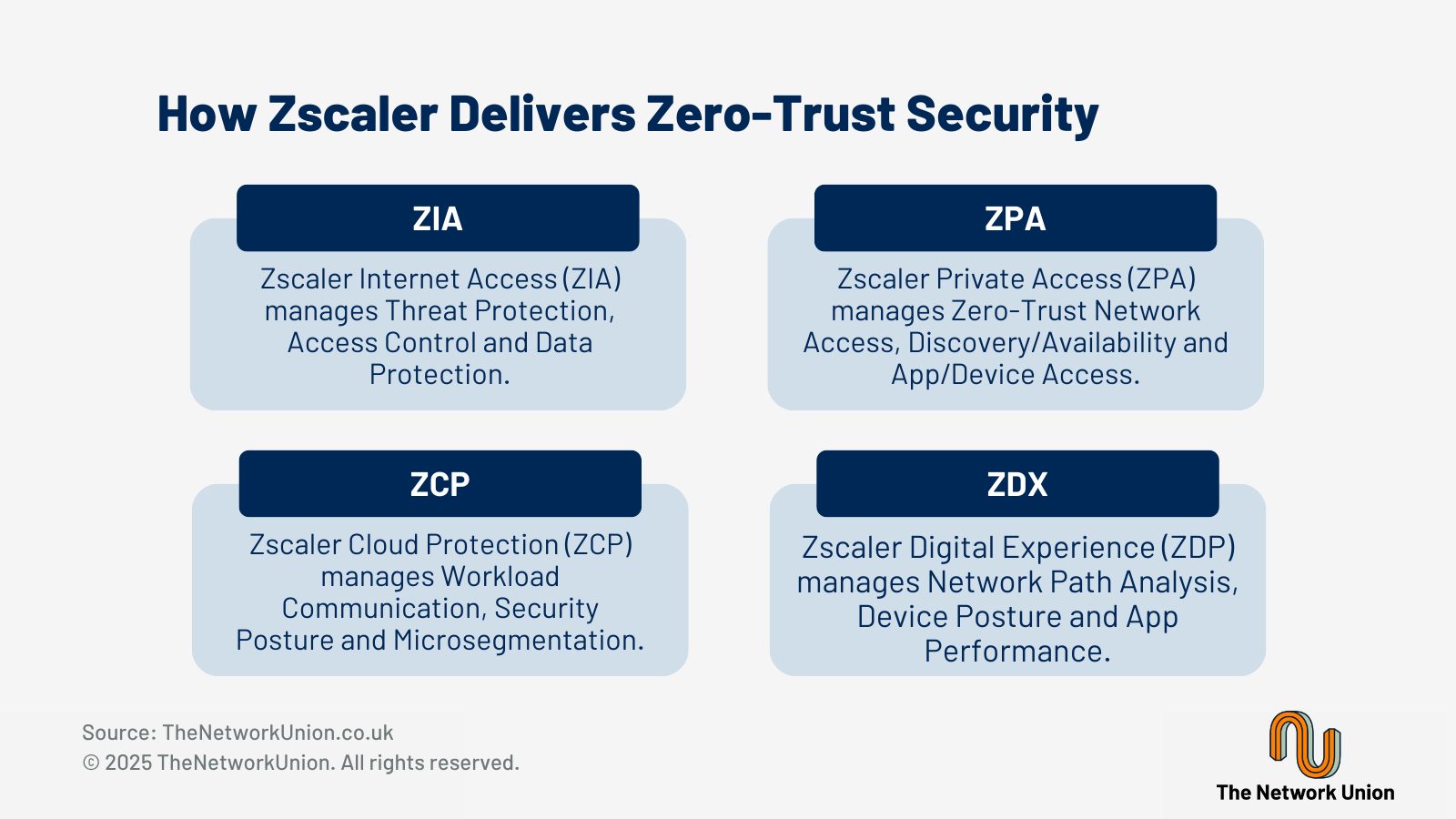
What is the Zscaler ZTNA solution?
Zscaler is a cloud-native solution that has a large geographic footprint with over 150 data centres around the globe, offering reliable and high-performing services close to users no matter where they are. For very large enterprises looking for ease of use and a great user experience with a comprehensive solution that is easy to deploy and scale, Zscaler is a “must consider” solution.
What are the pros and cons of Zscaler ZTNA?
Zscaler ZTNA Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 22/10/2024 02:56 PM | hyelland | 22/10/2024 02:56 PM | ✓ Zscaler’s solution removes the need for multiple endpoint agents as their ZTNA is built into its secure web gateway client. | ❌ The cost of deploying the Zscaler solution is higher than industry standard. |
| 2 | hyelland | 22/10/2024 02:56 PM | hyelland | 22/10/2024 02:56 PM | ✓ The solution is capable of supporting very large organisations, with the ability to take in up to hundreds of thousands of users and endpoints. | ❌ Lack of VoIP support for Zscaler Internet Access. |
| 3 | hyelland | 22/10/2024 02:56 PM | hyelland | 22/10/2024 02:56 PM | ✓ The Zscaler solution supports common UDP and TCP applications out-of-the-box, offering contextual data security and application access. | ❌ Endpoint device security support (compatibility) and security inspections are areas that need some improvement to compete with other pure-play security solutions. |
| 4 | hyelland | 22/10/2024 02:56 PM | hyelland | 22/10/2024 02:56 PM | ✓ The scalability of the Zscaler solution is above par for the industry, and it has strong capabilities for integration with the broader security ecosystem. | ❌ Traffic routing issues have also been noted by some customers upon initial deployment, although this isn’t uncommon during SD-WAN or security solution deployment. |
| Pros | Cons |
What is the Perimeter 81 ZTNA solution?
Perimeter 81’s solution is comprehensive and meets a variety of clients’ needs. One of the reasons that enterprises will choose to use Perimeter 81 is their long-term vision and customer success initiatives. Their product develops with client needs in mind, utilising emerging technologies.
What are the pros and cons of Perimeter 81 ZTNA?
Perimeter81 ZTNA Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 22/10/2024 02:54 PM | hyelland | 22/10/2024 02:54 PM | ✓ Perimeter 81’s solution allows administrators to view real-time user activity while streaming user audit logs to a SIEM provider, which may be desirable to allow network teams to monitor performance in-platform while the SOC works in their SIEM. | ❌ Logs are streamed to a SIEM and stored there, making them hard to find within the platform. |
| 2 | hyelland | 22/10/2024 02:54 PM | hyelland | 22/10/2024 02:54 PM | ✓ Their Zero Trust solution offers granular network segmentation by dividing access by user and application simultaneously with very granular identifiers and an intuitive browser-based application access portal. | ❌ Connectors and integrations into the broader security ecosystem are not as robust as other solutions available. |
| 3 | hyelland | 22/10/2024 02:54 PM | hyelland | 22/10/2024 02:54 PM | ✓ The solution also supports application access through IPSec or WireGuard. | ❌ The complexity of the solution leaves something to be desired when it comes to ease of deployment and user experience enhancements and improvements. |
| Pros | Cons |
What is the Cato Networks ZTNA solution?
Cato Networks is an appropriate choice for those organisations with smaller IT teams and no need for on-premises deployments. The vendor offers managed services and is very efficient at bringing on new sites. Early adopters are also interested in Cato Networks as they are one of the first full-SASE platforms available and are entirely cloud-based, offering immediate deployment with little to no customer involvement.
What are the pros and cons of Cato Networks ZTNA?
Cato ZTNA Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 22/10/2024 02:48 PM | hyelland | 22/10/2024 02:48 PM | ✓ Cato Networks’ solution incorporates Zero Trust, Secure SD-WAN and Firewall as a Service into their SASE offering, which exceeds customer expectations in most cases. | ❌ Cato Networks doesn’t offer an on-premise solution and has no integration with third-party monitoring platforms. |
| 2 | hyelland | 22/10/2024 02:48 PM | hyelland | 22/10/2024 02:48 PM | ✓ The vendor’s global private backbone allows for easy deployment and secure, optimised performance on a cloud-native solution. | ❌ Customer and technical support offerings could use improvement according to some customer feedback, and their SSO integration is still in a partially complete state. |
| 3 | hyelland | 22/10/2024 02:48 PM | hyelland | 22/10/2024 02:48 PM | ✓ Cato focuses on combining SASE and ZTNA together as a superior solution while offering managed services for those who don’t have the internal resources to dedicate to managing SD-WAN and ZTNA policies. | ❌ Their default SLA is sub-par for the industry, and professional services contracts are required to ensure higher SLAs. |
| Pros | Cons |
What is the Cloudflare ZTNA solution?
Cloudflare’s Zero Trust solution is high-performing, comprehensive and complex compared to other solutions on the market. It is suitable for clients with technical expertise and a robust IT team who is capable of deploying and managing complex solutions. Those with the capability to implement API integrations will benefit from the Cloudflare solution, as it makes it a good infrastructure solution for DevOps teams.
What are the pros and cons of Cloudflare ZTNA?
Cloudflare ZTNA Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 22/10/2024 02:51 PM | hyelland | 22/10/2024 02:51 PM | ✓ Cloudflare’s solution differentiates itself from the competition with their innovative approach to privately routing to IP subnets or individual hosts without VPN whilst enforcing ZTNA policies. | ❌ The complexity of implementing Cloudflare solutions lends to difficulty of deployment noted by some. |
| 2 | hyelland | 22/10/2024 02:51 PM | hyelland | 22/10/2024 02:51 PM | ✓ The company also offers Firewall as a Service, Cloud Access Security Broker (CASB), DNS resolution and filtering, HTTP/S inspection and filtering, and a Secure Web Gateway. | ❌ Customer feedback also notes a lack of device security support (in other words, compatibility with mobile endpoint devices like smartphones). |
| 3 | hyelland | 22/10/2024 02:51 PM | hyelland | 22/10/2024 02:51 PM | ✓ They also offer a transparent pricing model and strong integration capabilities with multiple identity providers as well as the broader cybersecurity ecosystem. | ❌ While Cloudflare’s DNS filtering performance is second to none, it could be more feature-rich with Artificial Intelligence and/or Machine Learning capabilities such as their competitors. |
| 4 | hyelland | 22/10/2024 02:51 PM | hyelland | 22/10/2024 02:51 PM | ❌ Complex implementation and low expectations for handholding by support teams mean that the solution requires a more technically-savvy implementation team for the customer. | |
| Pros | Cons |
What is the Fortinet ZTNA solution?
Fortinet is an affordable solution for organisations who wish to simplify their network security stack without the need for brand new innovations. Fortinet’s product line is a comprehensive solution that allows the integration and addition of more products to increase feature sets not available in the core functionality provided by Fortinet out-of-the-box.
What are the pros and cons of Fortinet ZTNA?
Fortinet ZTNA Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 22/10/2024 02:52 PM | hyelland | 22/10/2024 02:52 PM | ✓ The Fortinet solution feature set excels in areas of per-session access granted based on a verified user identity and device risk profile to better detect malicious actions or users. | ❌ Fortinet’s remote access solution still utilises VPN, despite features which allow it to operate with more control and performance than traditional VPN solutions. |
| 2 | hyelland | 22/10/2024 02:52 PM | hyelland | 22/10/2024 02:52 PM | ✓ Remote traffic is tunnelled to the ZTNA application proxy point, providing more security and better performance than traditional VPNs. | ❌ It has been noted that Fortinet and Fortigaurd’s firmwares could use more compatibility testing, as there are many occasions where upgrades have gone wrong and rollbacks may have been needed. |
| 3 | hyelland | 22/10/2024 02:52 PM | hyelland | 22/10/2024 02:52 PM | ✓ Offers strong SSO services, certificate management and guest control. | ❌ The solution lacks artificial intelligence and machine learning abilities for intrusion detection at firewall level. |
| 4 | hyelland | 22/10/2024 02:52 PM | hyelland | 22/10/2024 02:52 PM | ✓ Fortinet’s use of MAC address-based policies helps manage Zero Trust access more efficiently than vendors who default to IP-based policies. | ❌ Customer feedback indicates that Fortinet’s customer support response times are subpar compared to other industry leaders. |
| 5 | hyelland | 22/10/2024 02:52 PM | hyelland | 22/10/2024 02:52 PM | ❌ Fortinet’s interfaces for traffic logging and web filtering abilities are not very intuitive for the end-user. | |
| 6 | hyelland | 22/10/2024 02:52 PM | hyelland | 22/10/2024 02:52 PM | ❌ The FortiSIEM solution only provides marginal improvement over log analysis capabilities within the firewalls, but they do offer third-party SIEM integrations. | |
| Pros | Cons |
What is the Forcepoint ZTNA solution?
Forcepoint is a leading Zero Trust platform focused on observability and data security. The solution is a good choice for organisations that require a deeper knowledge of what data users and applications are accessing and what they are using that data for. Context related to user and application actions is a driving factor in organisations that choose Forcepoint, as they are industry leaders in this area.
What are the pros and cons of Forcepoint ZTNA?
Forcepoint ZTNA Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 22/10/2024 02:53 PM | hyelland | 22/10/2024 02:53 PM | ✓ Forcepoint’s solution stands out with its intelligent analytics focused on user behaviours and the observability of potential threats or bad actors. The solution allows administrators to see all user behaviour and associated context. | ❌ Forcepoint’s solution lacks in automation capabilities, as it is focused on analytics and behaviour that requires analysts and admins to take action on. |
| 2 | hyelland | 22/10/2024 02:53 PM | hyelland | 22/10/2024 02:53 PM | ✓ Forcepoint is a true Zero Trust platform – not a suite of products that work together to provide ZTNA, which makes scaling to larger organisations more manageable. | ❌ The future of Forcepoint’s Zero Trust platform is uncertain due to major changes in leadership and a lack of an industry-compatible roadmap. |
| 3 | hyelland | 22/10/2024 02:53 PM | hyelland | 22/10/2024 02:53 PM | ❌ Traditional Zero Trust core features like gateways, device and endpoint security are lacklustre and sufficient at best, while bleeding-edge technology and artificial intelligence are key differentiators. | |
| Pros | Cons |
What is the Check Point ZTNA solution?
Check Point is one of the largest global network cybersecurity vendors and has a significant chunk of market share. Organisations looking for a well-rounded solution with innovative approaches to Zero Trust, including seamless integration, full automation and reliable core features that are constantly undergoing improvement, will get the most out of Check Point solutions.
What are the pros and cons of Check Point ZTNA?
Checkpoint ZTNA Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 22/10/2024 02:50 PM | hyelland | 22/10/2024 02:50 PM | ✓ Check Point’s solution is comprehensive with features such as IPSec VPN tunnels, anti-spam and email security, application control, URL filtering, SSL connection management and mobile access support. | ❌ The Check Point solution lacks in reporting and visibility into threat origin and impact, although customers can make up for this with SIEM and threat intelligence integrations. |
| 2 | hyelland | 22/10/2024 02:50 PM | hyelland | 22/10/2024 02:50 PM | ✓ The solution is well-rounded and targets all key areas of Zero Trust models (including networks, people, devices, data and workload security) and allows for full automation and seamless integration to the cybersecurity ecosystem. | ❌ The solution usually requires a high level of technical ability to deploy, especially when implementing some of the more advanced features that the Check Point solution offers. |
| 3 | hyelland | 22/10/2024 02:50 PM | hyelland | 22/10/2024 02:50 PM | ✓ Advanced threat protection against zero-day attacks and their easy to use and deploy solution is commendable. | ❌ Customer feedback indicates that technical support pushes for professional services for complex issues and leaves some users feeling under-supported. |
| Pros | Cons |
What is the Cisco ZTNA solution?
Cisco’s solutions for ZTNA can be a good choice for any organisation that is already operating a Cisco environment. These organisations will already be familiar with the level of expertise required to properly design, deploy and manage Cisco products and will gain the most from Cisco’s offering.
What are the pros and cons of Cisco ZTNA?
Cisco ZTNA Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 22/10/2024 02:49 PM | hyelland | 22/10/2024 02:49 PM | ✓ The Cisco portfolio has a suite of offerings to comprise a Zero Trust solution that stands out in the market. | ❌ Cisco AnyConnect VPN requires integration with another solution like Duo Secure Access to get closer to providing true ZTNA for remote users. |
| 2 | hyelland | 22/10/2024 02:49 PM | hyelland | 22/10/2024 02:49 PM | ✓ Cisco’s Zero Trust solution includes integrated analytics, automated decision making, segmentation controls across whole infrastructures and seamless integration with Cisco’s identity management and multi-factor authentication products while adding impr | ❌ While Cisco has made several acquisitions to expand their security portfolio, solutions that comprise primarily of Cisco’s core enterprise network products require specific knowledge that apply to only Cisco products, and this can be difficult to implem |
| 3 | hyelland | 22/10/2024 02:49 PM | hyelland | 22/10/2024 02:49 PM | ✓ Cisco’s solutions offer cloud or on-premise as well as hybrid deployments. | |
| Pros | Cons |