In this article, you can access all of your resources including:
About the author: This article was written by Robert Sturt, read more about Robert's writing on Techtarget and Forbes.
We are the only company to have reviewed and tested 10 leading vendors & service providers to help IT decision makers understand current market leaders and their capability. Our analysis of leading SD-WAN vendors provides a comprehensive view of trends, offering valuable guidance for organisations comparing vendors and managed service providers across the US, UK and with national and global sites.
Follow each step listed below to help shortlist SD-WAN vendors and providers for your business.
Want to cut straight to the best SD-WAN vendors and providers for UK, US and Global businesses. We understand – IT decision makers are busy and your time is precious. You'll find a roundup of our top choices here. You can also jump to a more in-depth review for each product, along with our real-time, instant comparison tool to build your shortlist now.
BEST FOR GLOBAL, COMPLEX REQUIREMENTS
Cisco SD-WAN is suited to organisations requiring tight multi-cloud integration, supported via Cloud OnRamp. Testing demonstrated alignment with highly granular configuration, supporting the complex requirements of global networks. SASE cybersecurity capabilities are provided by Cisco Umbrella, which is well respected.
BEST FOR FULLY MANAGED GLOBAL SD-WAN
Aryaka's capability demonstrated strong features across unified management of networking and security. The core areas of value surround global WAN monitoring, last-mile circuit reporting, SASE integration, private backbone and detailed SLA reports across network security and application performance.
BEST FOR SD-WAN WITH HARDENED SECURITY
FortiManager centralises SASE network security management and analytics, enhancing compliance reporting. ADVPN performs efficiently in large mesh networks. Zero-Touch Provisioning is combined with FortiGuard security to provide reliable network performance and simplified management.
BEST FOR MULTI BRANCH-OFFICES
Meraki SD-WAN offers straightforward setup capability, security via Cisco Umbrella SASE integration, and an intuitive dashboard for network and device management. Meraki's capability is well-suited for multi-site organisations in retail or healthcare requiring secure branch connectivity.
BEST FOR GLOBAL CO-MANAGED SD-WAN+SASE DEPLOYMENTS
Cato SD-WAN demonstrated simple setup across integrated security including firewall, IPS and anti-malware, and intuitive management. Well-suited for organisations with limited IT resources needing to efficiently deploy and secure global networks with an SLA provided by their private backbone.
BEST FOR COMPLEX ROUTING WITH ANALYTICS
VMware SD-WAN's capability is strong across application performance optimisation. The featured enabled dynamic traffic steering and real-time routing. VMware is a comprehensive solution with SASE integration, zero-touch deployment and monitoring to simplify management for IT decision-makers.
BEST FOR GLOBAL FULLY MANAGED SD-WAN
Masergy's integrated SD-WAN and SASE with AIOps for optimised performance and security should make your shortlist if you are seeking out a fully managed provider. Masergy's service offers advanced cybersecurity with a global backbone making their solutions ideal for multinational Enterprise businesses.
BEST FOR SERVICE PROVIDER DELIVERY
Versa SD-WAN's capability revolves around simple cloud management via their Versa Titan Portal product. Features include Enterprise WiFi, bandwidth monitoring, and integrated SASE security. Well-suited for IT decision-makers needing to efficiently manage and secure complex networks.
BEST FOR SECURITY FIRST REQUIREMENTS
Palo offers clear capability and performance via their simplified Panorama management interface, integrated next-gen firewall security, and dynamic app performance optimisation. Well-suited for cloud-driven enterprises prioritising integrated SASE cybersecurity and simplified operations.
BEST FOR MICROSOFT AZURE INTEGRATION
Barracuda CloudGen WAN's native Azure Virtual WAN integration should make your shortlist if native Cloud integration is top of your requirements. Deployed from Azure Marketplace, it enables seamless SD-WAN and SASE rollout as a SaaS service, simplifying management for Azure customers.
For this article, we have created an at-a-glance checklist to help IT decision makers understand the areas which they must consider when comparing SD-WAN solutions.
Submit your details to receive a link to our SD-WAN buyers checklist, an at-a-glance Mind Map which details all of the areas you need to consider. Please check your junk folder if you do not receive an email within a few minutes.
We've listed the most popular SD WAN & Cybersecurity features which are requested by the majority of IT decision makers.
Consider your features based on what you already know. Global private backbone services are often considered by companies that currently use MPLS. In contrast, public gateways offer the ability to leverage multiple Internet providers to achieve the best possible global performance. If you're a national business, there is no need to select private or global as the benefits are not required.
Netify has researched the price points across vendors and service providers. In some instances, a key driver may be to save costs as a primary goal.
The number of sites and users will factor into your shortlist. For example, a larger Enterprise business will typically engage with different vendors and providers vs SME businesses.
Please review the information below and complete the form to finish the assessment.
Once you submit your details, each of the 3 vendors will reach out to you within 48 hours. Your results will be displayed once you have completed your details.
* Required field
Based on your selections, here are the companies that match your needs. Please check your mail over the next 24 hours - you will receive an introductory email from the vendors or providers listed below.
Unfortunately our system couldn't find an exact match but that doesn't mean there isn't a solution for you!
This assessment compares companies in our marketplace with everything you selected but the best way to find a solution is to connect with a Netify agent. We'll work directly with you to find a company which can fulfill your needs.
Based on your selections, here are the companies that match your needs. If you have questions, request to talk to a Netify employee using the button below.
Connect with us and we'll help you compare the market to find the perfect solution.
Netify is the first marketplace with a focus on SD WAN & SASE Cybersecurity. We employ researchers to list Gartner leaders, niche players and startups across WAN and security. The Netify advisory is available for free to help make sense of the decision making process by offering vendor briefings and tools to help your business find the right solution fit.
Unfortunately our system couldn't find an exact match but that doesn't mean there isn't a solution for you!
This assessment compares companies in our marketplace with everything you selected but the best way to find a solution is to connect with a Netify agent. We'll work directly with you to find a company which can fulfill your needs.
Fill out the form below and an expert will reach out to you within the next business day to develop a plan for your business.
In 2024, Meraki emerges as the best choice across SD-WAN Vendors, catering to the requirements of Medium and Large Enterprises. Meraki has been chosen based on Cloud integration, SASE security options, branch-office Wifi capability and support for remote workers.
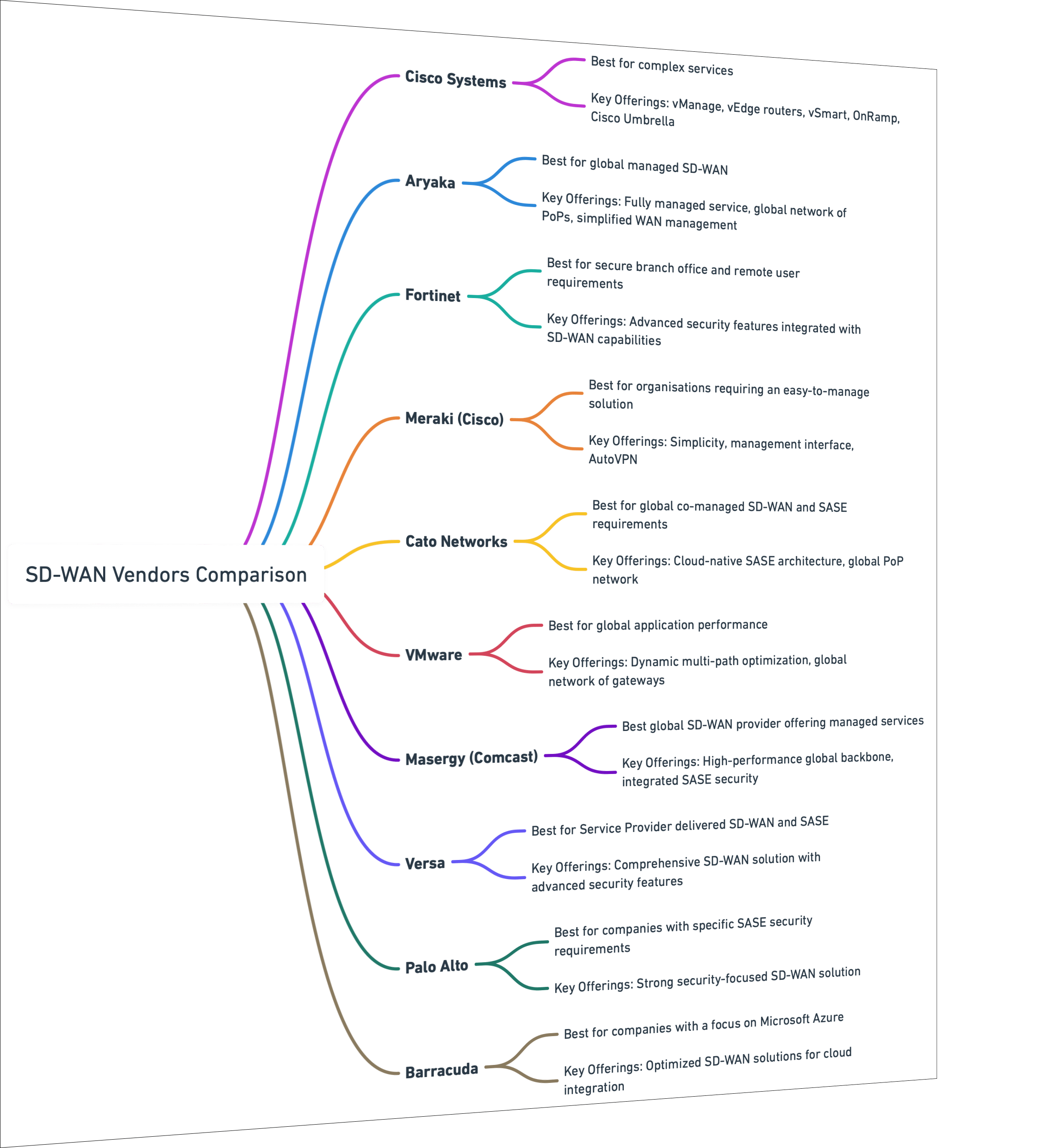
Robert Sturt has curated a list of the 10 best SD-WAN vendors and providers to fit the needs of most businesses. Included within each solution is a link to our hands-on test of each product.
Recognised by Gartner, as one of their magic quadrant leaders, Cisco SD-WAN is typically best for large complex Global Enterprise SD-WAN deployments.
| Evaluating Factor | Cisco SD-WAN |
|---|---|
| Gartner status: | Leader |
| Best for: | Complex Services |
| Reasons not to shortlist: | Lacks ease of use for network administrators that don’t have advanced SD-WAN knowledge |
| Stand-out features: | Application Aware Routing, Cloud OnRamp, Granular Control, Advanced Analytics, AIOps |
Cisco SD-WAN is known for its capability across Application Aware Routing (AAR), Cloud OnRamp and SD-WAN monitoring. With these features in mind, I focused our hands-on testing for these key areas to help understand the setup and overall capability of Cisco's SD-WAN solution, in order to determine best fit use cases.
Cisco SD-WAN AAR is a feature which optimises traffic based on applications and their overall importance. I started testing Cisco AAR by setting prioritisation for real-time VoIP traffic as this application is required by most enterprise businesses.
The configuration involved specifying the performance metric limitations by providing jitter (set at 30ms) and latency (set at 120ms). These values reflect real-world scenarios as each have been set to be on the verge of performance degradation when using VoIP.
To test if VoIP degraded, I applied traffic to the network causing a breach in the jitter and latency thresholds. The Cisco SD-WAN identified this issue and promptly re-routed the network traffic onto our secondary broadband circuit as per the configuration.
This meant that the Application Aware Routing was an effective method for managing heavy traffic for enhancing critical application experience.
Secondly, I tested Cisco SD-WAN Cloud OnRamp, a way to seamlessly integrate connections between branch offices and cloud services.
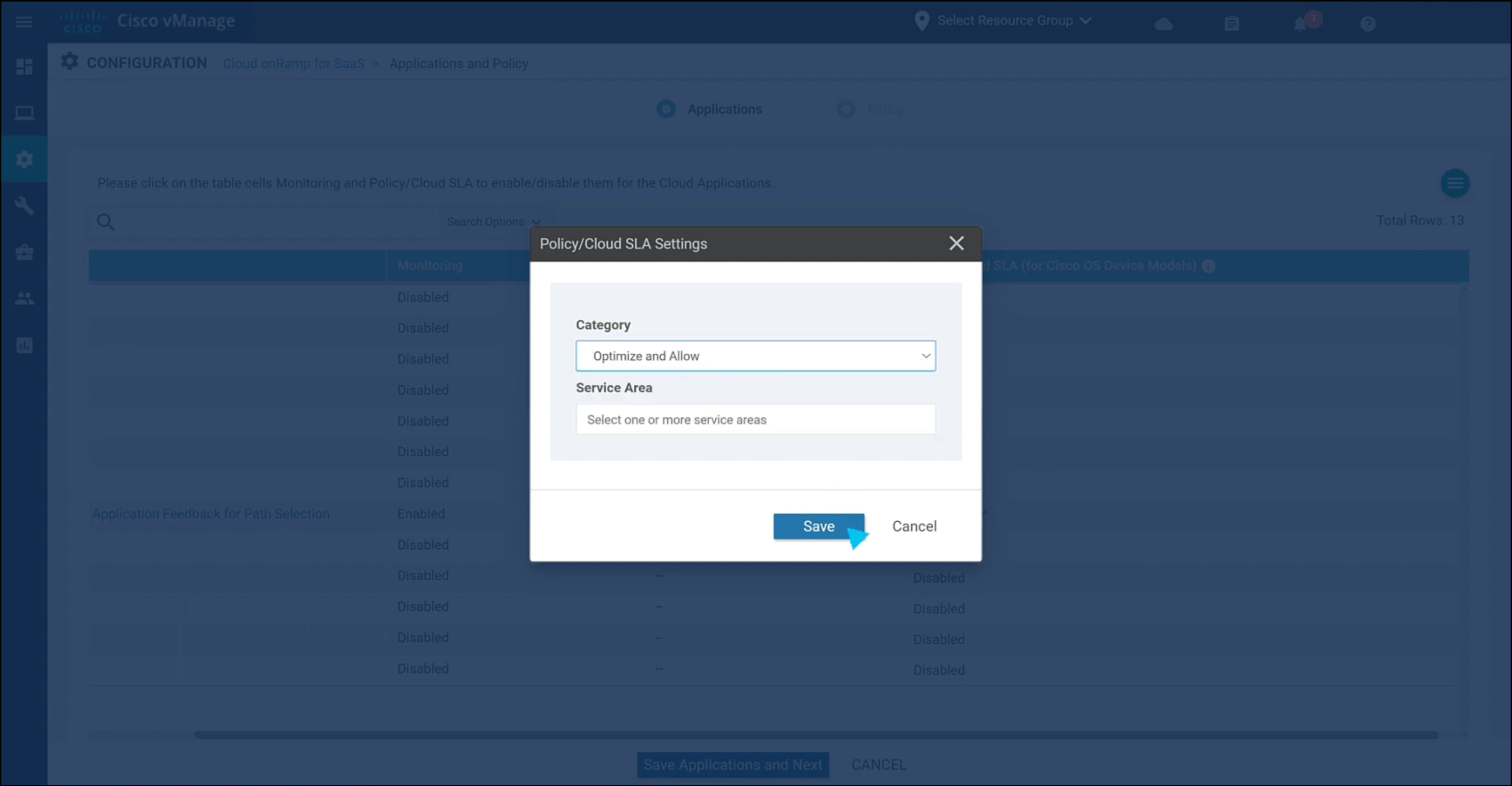
I connected a branch office network to Amazon Web Services (AWS) cloud using OnRamp. To do this I selected our cloud provider (AWS) and specified our Virtual Private Network settings in the manager interface.
Following configuration, I was able to monitor the stability and performance of the network via analytics and noted a significant performance improvement for the time taken to access our cloud-hosted applications.
In a real-world deployment this would significantly improve the stability of the network and provide users with a better experience within the network. I also noted that, given the ease of integrating cloud providers through a few menus, it means the cloud onramp functionality should significantly reduce overhead when introducing a multi-cloud integration to the network and reduce workload for network administrators.
Finally, I evaluated the analytics that Cisco SD-WAN provides to gain deep insights into the network. Using the dashboard, I started monitoring the traffic and metrics that were being recorded by the SD-WAN.
The analytics gave me a wide range of options such as drilling down into individual traffic flows, monitoring fluctuations in application performance and observe changes in bandwidth usage across the network. I focused primarily on the ability of Cisco SD-WAN to make forecasts based on predictive analytics.
I chose to consider this aspect as SD-WAN vendors are beginning to implement AIOps, artificial intelligence designed to pro-actively rectify network issues. This functionality suggested potential issues within the network before there was even the chance for the issues to cause any negative impacts on the network and gave me a proactive approach for implementing network optimisations in order to better use the network resources.
My testing of Cisco SD-WAN demonstrated the effectiveness of the AAR routing, Cloud OnRamp and analytical capabilities, providing network optimisations and simplifying deployment for a comprehensive SD-WAN solution.
Whilst the detail of functions such as traffic monitoring is very granular and allows a large amount of control, this did add some complexity that would be harder to work with for less SD-WAN knowledgeable network administrators.
In my opinion, Cisco SD-WAN offers a great solution for complex services, such as large scale enterprises, where an extra level of control/data reporting is required but would be hesitant to recommend it to small businesses where there isn’t quite the same need for granular control.
Cisco SD-WAN significantly cut WAN operational costs by 40% for Pfeifer & Langen Polska. The project involved setting up a traffic filtering policy between OSPF (Open Shortest Path First) and OMP (Overlay Management Protocol) as the central policy in the SD-WAN setup.
Pfeifer & Langen Polska highlighted Cisco's flexibility, noting their SD-WAN solution allowed the company to negotiate better with their connectivity providers. The network's independence from these providers meant they could consider other options without affecting the WAN infrastructure.
| Pros of Cisco Systems SD-WAN | Cons of Cisco Systems SD-WAN | Market Position of Cisco Systems SD-WAN |
|---|---|---|
| Enhanced Cloud Integration and Application Performance prioritisation features. | Cisco SD-WAN requires expertise to make the most of capability. | One of the largest SD-WAN vendors. |
| Extensive and capable management portal and capability. | Lacks some of the more innovative features of new SD-WAN players. | A Gartner magic quadrant leader due to a more-complete vision and ability. |
| Integrated Security Features, enabling network segmentation. | Reviews suggest remote access is one of the weaker Cisco SD-WAN features. | Has an extensive collection of other systems on offer that can be integrated. |
Aryaka provides access to a Global wholly owned network of PoPs with fully managed underlay (Internet connectivity) and overlay (SD-WAN and SASE cybersecurity). It provides performance visualisation, security observability control and pro-active troubleshooting. Aryaka is best for organisations with global, fully managed services needs with standard requirements.
Aryaka received the Stevie Gold in Software-Defined Infrastructure, the 2021 Internet Telephony SD-WAN Product of the Year Award.
The Aryaka FlexCore network is central to delivery of their overall capability which includes MPLS network migration, Last mile Internet, Cloud and SaaS acceleration, remote access, next generation Firewall and Secure web gateway. These features collectively enhance the SD-WAN system offering customers a comprehensive solution.
Although Aryaka is a highly capable SD-WAN solution, the capability does not extend to complex configuration needs. Aspects such as their last mile procurement and circuit inventory with SLA performance metrics make managing their SD-WAN solution simple on an every day basis. The SLA reporting is generated based on extensive reporting across circuit utilisation, downtime, latency, and jitter.
Customers choose Aryaka because of their capability to deliver SD-WAN as an underlay and overlay MSP with the addition of a wholly owned private IP backbone which spans 40 PoP locations. Aryaka provides excellent latency and jitter performance across Global SaaS cloud applications.
One example of Aryaka in use is Solenis. Solenis has a global presence in over 100 countries and more than 5,000 employees. Their business faced significant challenges with their network infrastructure. Slow file transfers, delayed database syncing, and poor application performance were hindering critical business processes across order management and delivery. After evaluating various solutions, Solenis chose Aryaka’s SmartConnect SD-WAN-as-a-Service for its ability to guarantee application performance in remote regions.
Aryaka’s proprietary byte-level data deduplication algorithm, Advanced Redundancy Removal (ARR™), significantly improves network throughput by removing redundancy from WAN traffic. This has led to bandwidth utilisation reductions of up to 99% and a decrease in round trips by as much as 95% in some customer deployments.
The deployment of Aryaka’s SD-WAN solution enabled Solenis to significantly enhance the performance of its critical business applications.
| Pros of Aryaka SD-WAN | Cons of Aryaka SD-WAN | Market Position of Aryaka SD-WAN |
|---|---|---|
| Aryaka's SD-WAN is a fully managed service, which means businesses don't have to worry about managing their WAN infrastructure. | Aryaka's SD-WAN is a managed service, which means businesses may have less control over their network infrastructure compared to a self-managed solution. | Aryaka provides integrated SD-WAN and SASE functionality for global networking. |
| Aryaka's SD-WAN provides improved application performance through a combination of WAN optimisation techniques. | While Aryaka's SD-WAN can lead to cost savings in some areas, such as reduced IT staff workload, the service itself can be expensive. | Aryaka combines both technology vendors and managed service providers (therefore catering to customer’s tailored needs). |
| Aryaka's SD-WAN is easy to deploy and can be scaled up or down to meet changing business needs. | With Aryaka's SD-WAN, businesses are dependent on Aryaka for their network infrastructure which could be viewed as a risk. | Aryaka must continue to invest in its SASE portfolio to remain competitive against larger SD-WAN vendors and adapt to evolving market demands. |
Is Aryaka SD-WAN integrating AI?
Aryaka plans to integrate AI for network security and observability.
Future development
Whilst Aryaka does provide a fully managed service, it will likely require further investment into its SASE portfolio in order to compete with larger SD-WAN vendors.
Aryaka's SD-WAN solutions offer a range of services for diverse business needs, with pricing structured to match. The SmartConnect service, Aryaka's core SD-WAN offering, starts at $150 per site each month. This plan includes a network appliance, advanced application control and visibility, along with a fully managed service, providing a cost-effective option for global connectivity and application performance optimisation without a large initial expense. For businesses looking for an integrated network and security solution, Aryaka Prime begins at under $150 per site.
Fortinet is known for their history of delivering highly rated Firewall capability via their custom ASIC WAN edge hardware. The Fortinet Secure SD-WAN product supports security sensitive cloud applications for both national and global enterprises across 31,000 customers.
Fortinet's Secure SD-WAN solution is also part of their Unified SASE offering, integrating SD-WAN and security components into a single platform.
Fortinet was named a 2023 Gartner Peer Insights Customers' Choice for SD-WAN for the fourth consecutive year and received the highest reviews of all vendors in the SD-WAN market as of December 2022, with 96% of reviewers willing to recommend Fortinet's Secure SD-WAN solution.
Standout features include next-generation firewall (NGFW), advanced routing, and ZTNA application gateway functions to ensure branch-office, cloud SaaS applications and remote workers can all access resources without compromising security. Fortinet is currently recognised by Gartner within the SD-WAN magic quadrant.
Fortinet is best for companies with a need for branch-office and remote worker SD-WAN with extensive firewall capability requirements. We also note that Fortinet has been widely adopted by Service Providers and is offered as an MSP proposition.
TH True Milk transformed its network across 400 sites with Fortinet Secure SD-WAN. The solution improved connectivity for 3,000 users, boosted performance by 50x, and cut costs by 45% annually.
Deployment took minutes instead of days. Network tickets dropped by 70%. FortiManager and FortiAnalyzer provided single-pane management and reporting. With Fortinet, TH True Milk secured their network, optimised traffic, and delivered high application performance. The IT team can now easily monitor the network. Fortinet proved to be the best choice for performance, cost savings and ease of use.
Businesses should choose Fortinet if they require a strong WAN edge solution to support branch-offices and remote workers. If strong Zero-trust is at the core of your needs, with next generation Firewall, Fortinet is a good choice. Readers should note that DIY management requires significant expertise - Fortinet is available from numerous MSP's and service providers.
| Pros of Fortinet SD-WAN | Cons of Fortinet SD-WAN | Market Position of Fortinet SD-WAN |
|---|---|---|
| Fortinet's Secure SD-WAN solution is known for its deeply integrated advanced security features. Unlike many SD-WAN solutions that require additional security overlays, Fortinet combines networking and traffic shaping with next-generation firewall capabilities in a single solution | While Fortinet aims to simplify WAN operations, SD-WAN architectures, in general, can be more complex to manage compared to traditional WAN solutions. | Fortinet is recognised as a Leader in Gartner's Magic Quadrant. |
| Fortinet provides centralised management through FortiOS, which simplifies the operation and management of the WAN. This allows for zero-touch provisioning, enabling quick site deployment. | Some organisations may find that the cost savings expected from SD-WAN are not fully realised, especially if they need to upgrade their existing infrastructure to support the SD-WAN platform. | Fortinet has a strong market share via range channel partners. |
| Fortinet's are investing in their global AI assistant to help IT teams improve networking decisions. | Although Fortinet's SD-WAN includes integrated security, it may still lack breadth of security offered by some of the newer SD-WAN vendor solutions. | Fortinet are viewed as a cost effective provider with good ROI. |
Is Fortinet SD-WAN integrating AI?
Introduces enhanced AIOps capabilities across their SD-WAN, wired/wireless, and 5G/LTE gateway portfolio. This is in the form of a digital experience monitoring, an AI-based assistant, and improved internet and application performance.
For small setups, the 40F model starts at £950, while medium businesses might look at the 60F model priced at £1,250. Larger organisations have options like the 100F at £5,350, and for very large or enterprise-level needs, the 200F model is available at £12,250, showcasing a significant range based on capability needs, from SSL Inspection Throughputs of 310mb for smaller setups to 4gb for the largest configurations. Source: https://www.netify.com/learning/fortinet-sase-overview-pricing-examples
Meraki is known for their ability to deliver SD-WAN to branch-office and remote users with simplicity and unique features, including support for CCTV (smart cameras), sensors, cloud services, remote users and an excellent WiFi capability.
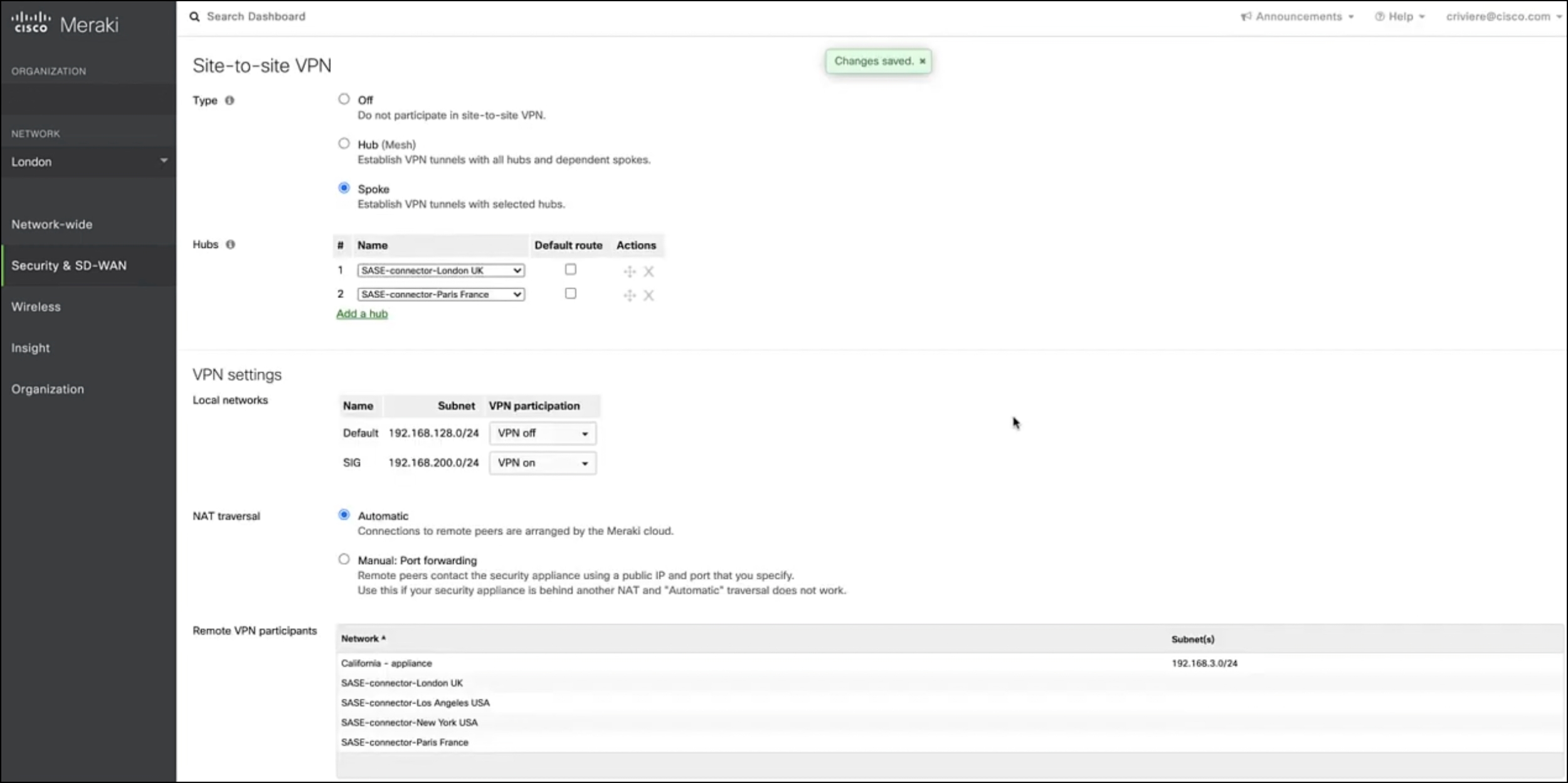
One of their stand-out capabilities is their management interface together with AutoVPN, which enables the setup and deployment of SD-WAN in minutes. Meraki deployments are also effective at supporting multiple Internet circuit types (including support for cellular) via their capability across failover and prioritisation using policy based routing and dynamic path selection. Meraki can deliver the complete solution across Wireless and Switching with unified SASE capability.
Meraki is viewed as the best solution for healthcare and retail. In part, this is due to their strong Wifi, CCTV and sensor capability which fits with the needs of these sectors. However, most business can leverage Meraki benefits, which include ease of configuration, strong partner support and significant product investment from Cisco.
Reading School District faced network management challenges with 19 schools to manage. The School switched to a full-stack Meraki solution, which included over 1,400 access points to enhance wireless coverage and simplify network management.
Mr Hiestand (the district's sole Network and Systems Administrator) needed an easily managed system without sacrificing performance. Meraki's solution provided a unified management dashboard, allowing for quick, district-wide updates and configurations to significantly reduce the potential for errors and administrative overhead. This shift has enabled the district to focus on improving classroom technology and student engagement.
For businesses requiring an SD-WAN for numerous branch-office sites, Meraki represents a good solution. CCTV, Wifi, and sensor technology are often a great fit for specific use-cases across the retail and healthcare sectors. Alongside these features is a good overall SASE capability, switching and remote user solution (using their mobile device management features).
| Pros of Meraki SD-WAN | Cons of Meraki SD-WAN | Market Position of Meraki SD-WAN |
|---|---|---|
| Meraki SD-WAN offers a user-friendly, web-based dashboard for managing the entire network. | While Meraki SD-WAN is viewed as a cost-effective solution, some businesses report costs rise significantly as more features are required. | Cisco Meraki SD-WAN has huge market presence with a large global partner base. |
| Meraki's Auto VPN technology simplifies the complex process of VPN configuration. | Meraki's focus on simplicity and user-friendly design sometimes comes at the cost of granular control. | Financial details about Cisco's specific investment in the SD-WAN market, including Meraki, are limited. |
| Strong CCTV and branch-office Wifi capability with excellent reporting. | Meraki SD-WAN requires the use of Meraki hardware for its full set of features and benefits. Think carefully if your organisation is invested in other vendor solutions. |
Is Cisco SD-WAN integrating AI?
Building their network platform from the cloud up for automation and AI, focusing on network health and intelligent recommendations. Meraki's product strategy includes focusing on AI networking, integrated security, scalability, and cloud onramp capabilities.
Meraki offers a range of SD-WAN products and services, including the MX67 Secure SD-WAN Plus License at approximately $661.22 for a year's support, and the Enterprise License for site redundancy across three locations at about $17,000 for three years, alongside a comprehensive design, build, and managed service priced per day. Prices are based on recent exchange rates and may vary.
In Q3 2023, Cato were recognised by Gartner as a leader in their GigaOm report across product leadership. The Cato SD-WAN solution provides cloud-native SASE architecture to deliver a consistent level of service across all elements of their capability. In simple terms, Cato are delivering the complete Cloud stack across SASE and SD-WAN which reduces complexity.
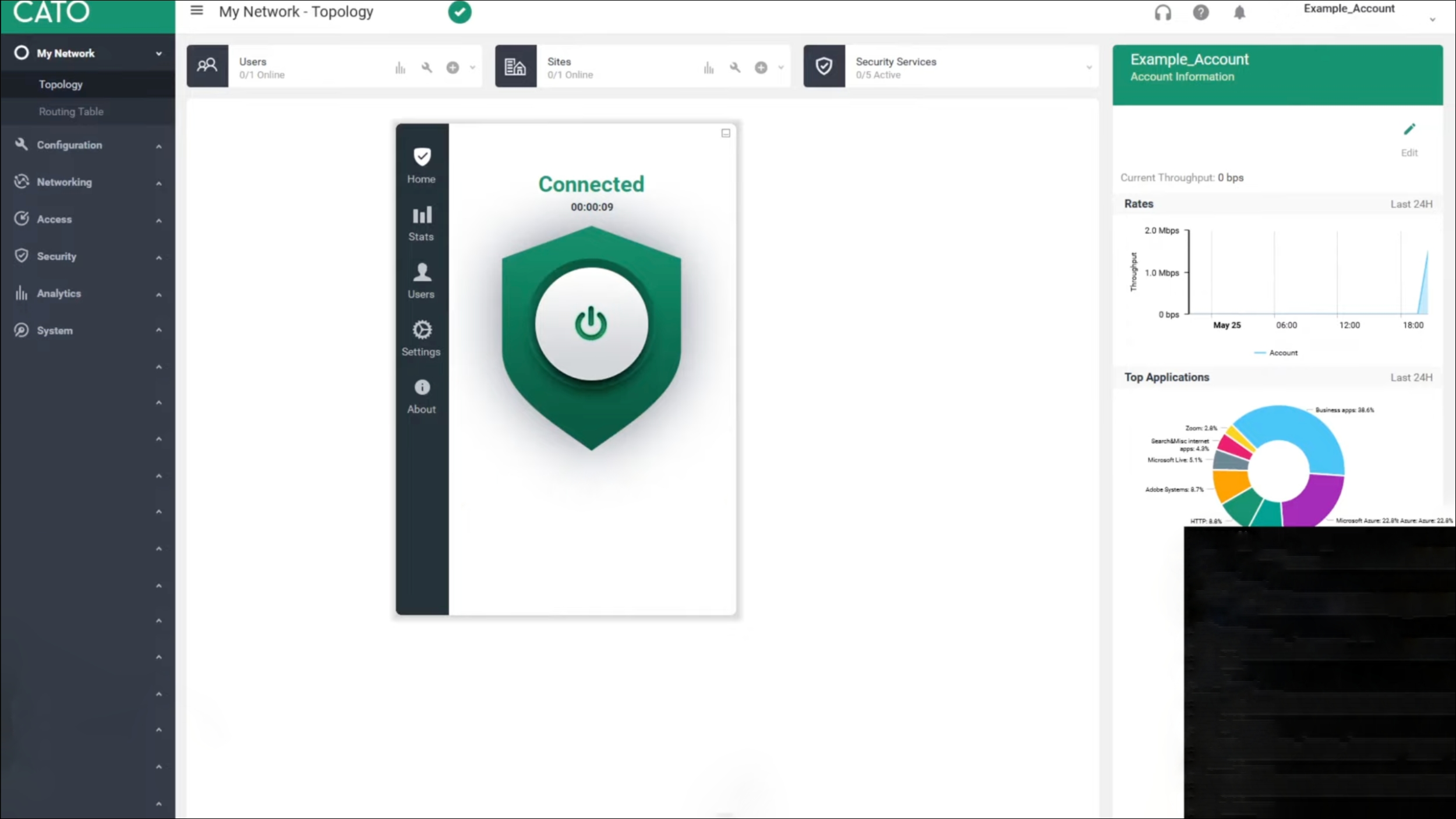
While Cato can deliver fully managed services, most customers opt for co-managed, which ensures the core capability is setup and deployed but allows IT teams to quickly make the changes they need. Comparable to Aryaka, Cato operate a network of global PoP locations to enhance application and cloud access performance.
Cato is best for businesses which require global co-managed services. While Cato does offer fully managed services, their capability is more aligned with businesses requiring initial setup and support but, day to day control of the SD-WAN.
Brake Masters is a 71-site auto-repair chain, their business switched from MPLS to Cato's SD-WAN. The change increased bandwidth by 30x and ended weekly outages. The previous MPLS network bandwidth was low and they company was experiencing issues with lines poor Wi-Fi.
After comparing 10+ vendors, IT Director Steve Waibel picked Cato for their capability across setup, management and cost. The new solution enables proactive network monitoring. Steve praised Cato's affordability and ease of opening new locations - he says it greatly improves on their six years with MPLS.
It should, however, be noted that if your business is global and requires a fully featured end-to-end single vendor SASE and SD-WAN co-managed solution, it is important to understand that Cato is a solution which is not highly customisable which may mean complex Enterprise networks should look elsewhere for their SD-WAN solution.
| Pros of Cato SD-WAN | Cons of Cato SD-WAN | Market Position of Cato SD-WAN |
|---|---|---|
| Cato SD-WAN is known for its simplicity and quick deployment capabilities. The Cato Socket, a key component of their SD-WAN solution, facilitates easy setup and immediate operational status, making the process hassle-free for businesses of all sizes. | Cato Networks might lack some of the advanced features and the broad market acceptance that established competitors possess. | In Q3 2023, Cato were recognised by Gartner as a leader in their GigaOm report across product leadership. |
| Cato integrates comprehensive security features directly into its SD-WAN solution, including a Secure Web Gateway, advanced anti-malware, and Intrusion Prevention System (IPS). | Unlike Aryaka, customers must research and purchase their own underlay connectivity (ISP services). | Cato Networks has been continuously adding new features, with SSL inspection in the cloud being released in 2021. This commitment to ongoing innovation demonstrates that Cato Networks is dedicated to staying ahead of the curve and delivering cutting-edge solutions to its customers. |
| Cato offers a global private backbone that significantly enhances the performance of international traffic. | To fully leverage Cato's SD-WAN solution, some organisations might need to replace their current network infrastructure or make significant changes to it. | In 2017, Cato Networks' SD-WAN was recognized for its cloud-native architecture and the potential of its upcoming SASE features. |
Is Cato SD-WAN integrating AI?
Cato Networks is actively exploring the use of Machine Learning (ML) and Artificial Intelligence (AI) to enhance the security and effectiveness of their Secure Access Service Edge (SASE) product, which includes its SD-WAN solution.
We do not have specific examples of Cato SD-WAN pricing but, Fisher & Company, an automotive company, was able to lower its connectivity costs by 70% by using Cato's SD-WAN instead of MPLS. They were previously spending $27,000/month for a managed, secure MPLS service, with a 10 Mbps U.S. to Mexico connection alone costing $7,000/month.
VMware's work within the virtualisation market means they are a well recognised and respected brand in the networking space. With the purchase of VeloCloud, VMware has integrated an SD-WAN and SASE capability to create a number of features.
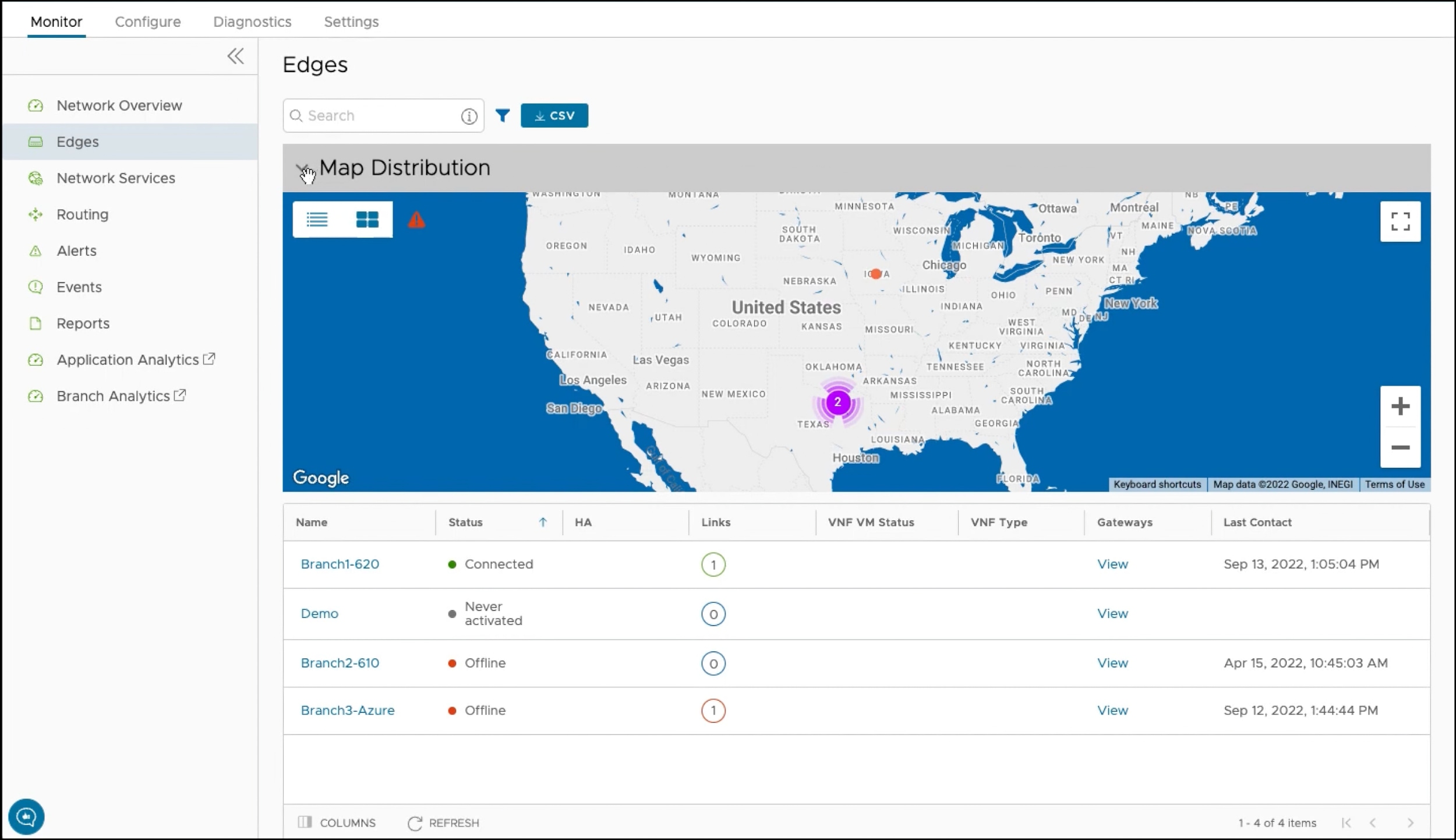
One of these features is dynamic multi-path optimisation with access to a network of global gateways meaning their solution has been adopted by their existing multinational customer base. Similar to Cisco SD-WAN, VMware is also capable of network segmentation which is aligned well with significant cloud capability
VMware are best for global businesses that require the best possible application performance. With global Internet connected gateways, VMware are recognised for their ability to ensure applications traverse the Internet with low latency.
First, if you are a current customer of VMware with Global requirements, VMware should make your shortlist. The global network of cloud gateways are connected to multiple ISP's which in turn is leveraged by their dynamic multi-path SD-WAN application routing meaning Global Enterprises should also consider the VMware solution. Readers should note that VMware is typically available via Service Providers which presents a further comparison task when conducting research.
Stolt-Nielsen replaced its complex MPLS network with VMware SD-WAN through Expereo. The old setup had issues with cost, flexibility, and management across 40+ global sites.
VMware SD-WAN connected Stolt-Nielsen's apps and guarantees quality across their users. The SD-WAN solution supports easy M&A integration too. Rollout took just 3 months, down from 1 year. with sites seeing a major bandwidth and speed boost.
New sites now take days, not months to install which offers significant agility. Management is also simpler with 1 portal vs. 6+ used previously.
| Pros of VMware SD-WAN | Cons of VMware SD-WAN | Market Position of VMWare SD-WAN |
|---|---|---|
| VMware SD-WAN enhances application performance across the network by leveraging dynamic multi-path optimisation. | VMware SD-WAN does not provide an integrated solution for WLAN, LAN, and network security within a single offering. | Recognised as a Leader in Gartner's Magic Quadrant. |
| The platform integrates comprehensive security features, including end-to-end segmentation, advanced threat protection, and the ability to insert security services wherever needed. | Some users have found VMware SD-WAN to be costly and have expressed concerns about the lack of transparent pricing information. | Roadmap is aligned with current and emerging customer needs, including cloud transport and AI functionality. |
| VMware SD-WAN supports a highly scalable and flexible network architecture. | While VMware SD-WAN is praised for its features and performance, some users have reported challenges with finding comprehensive documentation and receiving support for complex issues. | Recognised for strong customer experience based on Gartner client interactions, Peer Insights data, and high Net Promoter Score. |
Is VMWare SD-WAN integrating AI?
VMware is integrating AI and ML into their SD-WAN solution to enhance network operations and application performance. The Edge Network Intelligence delivers enhanced AIOps capabilities to reduce SD-WAN operations costs and provide visibility to end-to-end application performance.
VMware's SD-WAN offerings include the VeloCloud Premium Edition with a 1-year subscription for 1 Gbps bandwidth at $6,831.99, and the Enterprise Edition priced at $4,779, alongside a 5-year 10 Gbps bandwidth plan with support at $15,728, and variable pricing for the 10 Mbps production support edition between $326 and $928. The UK Government Digital Marketplace lists VMware SD-WAN at £438.45 annually.
The first true traditional service provider to make our list of best SD-WAN providers. Netify have worked successfully with Masergy (now Comcast) since 2010, as customers of large telcos became disgruntled with service and support.
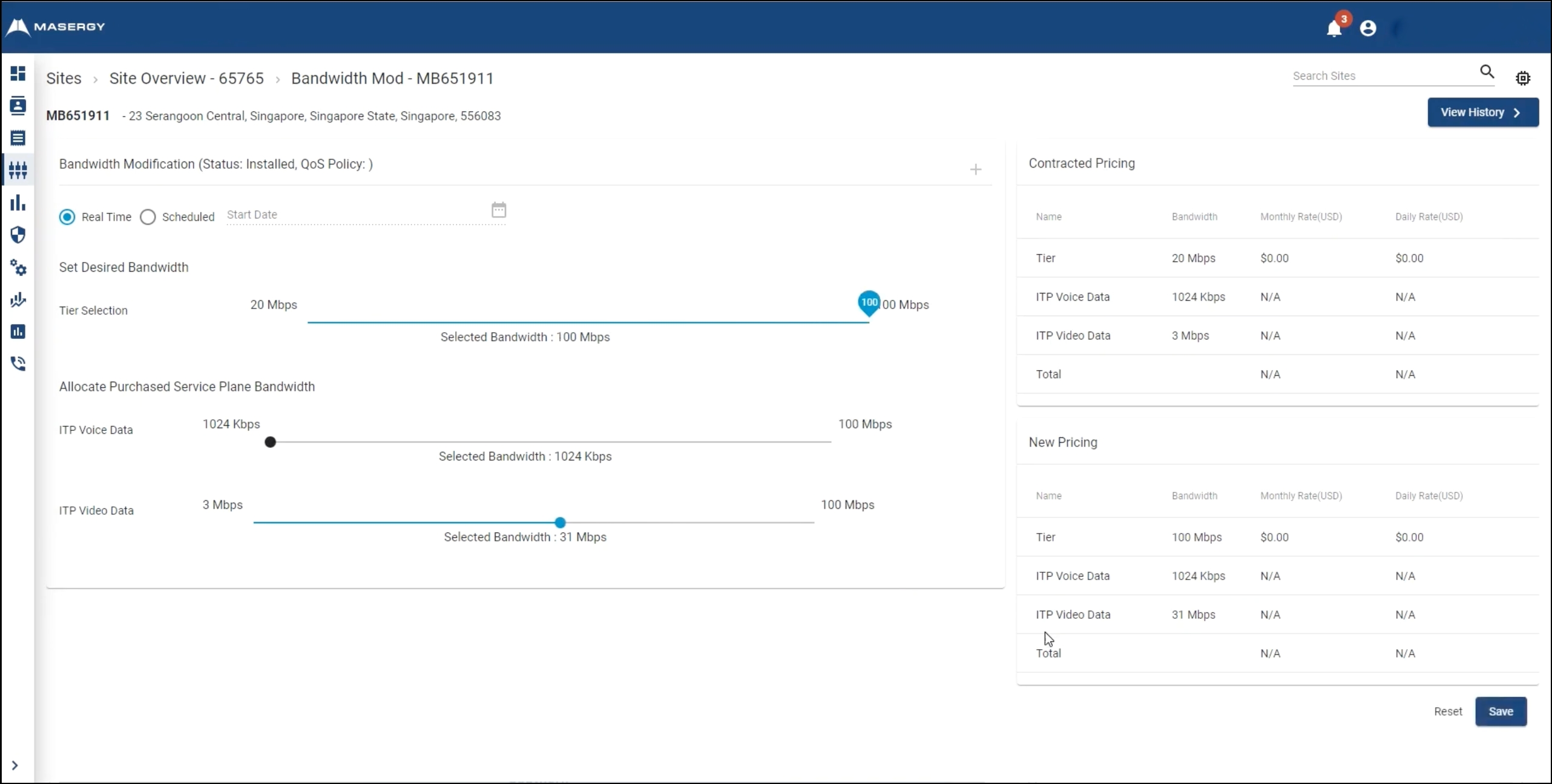
Not only does Masergy offer highly rated support, they also operate one of the highest performing global backbones across latency and jitter. We note the capability of Masergy's AIOps and Network Analytics to deliver actionable insights into network security and application performance. There's also integrated SASE security which is delivered by their UTM (Unified Threat Management), NGFW (Next Generation Firewall) with advanced IDS (Intrusion Detection System). The entire Masergy capability is wrapped into fully managed services which is capable of delivering connectivity across their own backbone of via OTT (Over the Top) where Masergy will SLA 3rd party Internet connectivity.
Customers looking to outsource managed services to a traditional service provider should consider Masergy. The Masergy capability integrates fully managed SD-WAN and SASE security across a global infrastructure with flexible managed service options. All backed up by a high Net Promoter score.
Eurostar runs high-speed trains linking England, France and Belgium. The goal of engaging Masergy was to migrate critical apps to Amazon Web Services (AWS) cloud meaning that the network is vital for access and security.
With a small IT team, Eurostar wanted a managed provider to support this shift. It needed an MSP with traffic engineering, bandwidth on demand, and strong cybersecurity. Masergy created a custom software-defined WAN with direct AWS links, which intelligently delivers primary and backup connectivity globally. Eurostar can adjust bandwidth in real time as needed.
Masergy are best for global service provider managed services. The combination of their backbone, adoption of AIOps, and high Net Promoter score means your applications perform well and your solution support is firmly in place for when issues occur.
| Pros of Masergy SD-WAN | Cons of Masergy SD-WAN | Market Position of Masergy SD-WAN |
|---|---|---|
| Masergy SD-WAN includes built-in security capabilities such as next-generation firewalls with Unified Threat Management (UTM), advanced Intrusion Detection Systems (IDS), and end-to-end IPsec data encryption. | While Masergy SD-WAN offers a comprehensive set of features and managed services, the cost can be a significant factor for some businesses. | Recognised for their pioneering approach in managed SD-WAN services. |
| Masergy offers a global network that ensures high performance and reliability for SD-WAN sites, committing to 100% service availability for SD-WAN sites configured for high availability and for direct cloud connections architected for redundancy. | While Masergy's managed SD-WAN service is designed to simplify network management, it may also result in limited visibility and control for businesses that prefer to have hands-on management of their network. | Designed for companies seeking a single provider global network for their bespoke SD-WAN design and deployment. |
| High Net Promoter score recognising their ability to deliver excellent customer service. | Masergy's service and support does carry a premium, businesses looking for low cost SD-WAN should look elsewhere. | The best-of-breed approach relies on external vendors for certain security and network functionalities. |
Is Masergy SD-WAN integrating AI?
Masergy has introduced AIOps, an industry-first integrated AI-based solution for network, security, and application optimisation. This digital assistant, embedded into Masergy's Intelligent Service Control customer portal, acts as a virtual engineer, providing intelligent alerts and recommendations to enhance application performance, predict bandwidth needs, and optimise network throughput using anomaly detection and predictive analytics.
| Masergy SD-WAN Service | Estimated Monthly Cost Per Location |
|---|---|
| SD-WAN as a Service | $100 to $200 |
We hope to research pricing further during 2024. Masergy do not publish SD-WAN pricing data.
Versa SD-WAN offers true multi-tenancy with sophisticated and customisable analytics and reporting. These features mean that Versa is widely adopted by service providers which, in turn, deliver managed services to their customer base.
Versa also offers a Unified SASE solution that natively integrates SD-WAN and SSE components into a single architectural framework.
Versa is also capable of delivering highly complex requirements along side standardised SD-WAN features to meet the needs of most organisations. Where simpler requirements are concerned, Versa is one of the most cost effective solutions on the market which is capable of offering a broad set of SASE and SD-WAN features.
Gartner recognise Versa within the leader section of their magic quadrant, which is part due to highly capable UTM (Unified Threat Management) and their single pass architecture which is designed to reduce latency.
Versa are best for national companies with generalised needs. The Versa capability is excellent across all SD-WAN features from SASE security to traffic optimisation. Although Versa is used for Global companies, we would recommend their solution for national requirements.
Versa is a cost effective alternative to the usual suspects of Meraki and Fortinet. There's no IP backbone to leverage with Versa but the solution is delivered via their Cloud presence. There is a focus on SASE security, Versa have been recognised by Gartner for their approach to networking and security. Overall, Versa should be selected based on their strong application steering and comprehensive SASE solution.
The dual-management solution allowed the company to maintain control over configurations while the service provider handled uCPE deployment and monitoring.
Key benefits included optimised bandwidth usage, intelligent traffic steering, centralised orchestration and integrated security. The Versa Secure Cloud IP platform enabled the firm to achieve its goals of a topology- and vendor-agnostic network that supports both on-premises and cloud applications with scalability and automation.
| Pros of Versa SD-WAN | Cons of Versa SD-WAN | Market Position of Versa SD-WAN |
|---|---|---|
| Versa SD-WAN offers a unified solution that integrates advanced security services, such as next-generation firewalls and Unified Threat Management (UTM), with its SD-WAN capabilities. | Some users have reported that the management interface of Versa SD-WAN can be complex and overwhelming. | Recognised as a Leader in Gartner's Magic Quadrant. |
| Versa's SD-WAN solution features dynamic policy-based path selection, which optimises application performance by intelligently routing traffic based on real-time network conditions. | Versa SD-WAN has been noted to lack substantial WAN optimisation functionality. | Unified SASE market share leader based on Dell’Oro Group Q3 2023 report. |
| Versa SD-WAN provides a range of deployment options, including on-premises, cloud, and blended models. | Versa SD-WAN is perceived to have a lower market presence and visibility outside of the service provider realm. |
Versa Networks has introduced AI and ML-powered enhancements across its product line, including its SD-WAN solutions. These advancements leverage sophisticated analytics and true multi-tenancy to provide enhanced networking and security capabilities.
Versa Networks offers SD-WAN services such as Versa Secure Access, providing secure SD-WAN access for remote users from $10 monthly per user, and the Versa Cloud Services Gateway 730 priced at $1,000, with the WLAN access variant at $1,400.
Palo Alto (Prisma SD-WAN), a leader in the Gartner magic quadrant, is used by large Enterprise customers with complex or granular cybersecurity requirements. With this in mind, Palo is often viewed as difficult to setup and configure due to the need to meet the demands of complicated security architecture.
Palo Alto Networks' Prisma SD-WAN is part of their Unified SASE solution, combining SD-WAN and security services.
Palo Alto SD-WAN won CRN's 2022 SD-WAN Product of the Year Award and has been recognised for continued innovation and leadership position by industry analysts like Frost & Sullivan and Gartner.
The core capability of Palo Alto SD-WAN surrounds their next generation Firewall offering but there are enhancements arriving to keep pace with SD-WAN innovations. These include packet duplication and FEC (Forward Error Correction) to help improve delay sensitive application performance. Over the next 18 months, Palo Alto Networks have stated their intent to enhance application acceleration, SASE enhancements and FEC and packet duplication.
Palo Alto is generally best for organisations which have a need to leverage their next generation SASE security capability. Companies are aware of their strong history and security focus over many years. The Palo SD-WAN solution has been tested across application aware routing demonstrating their commitment to SD-WAN features.
Your business should shortlist Palo Alto if you have complex and specific security needs. Palo is also recognised as a vendor for large Global Enterprise businesses - Gartner have stated that Palo has a focus on the larger corporate market.
Nuffield Health transformed their cybersecurity strategy by partnering with Palo Alto Networks. By deploying Palo Alto Networks ML-Powered Next-Generation Firewalls, Prisma Access and Cortex XSOAR.
The Palo integrated solution delivers secure, direct-to-app connectivity for patients, members, and customers across Nuffield's 37 hospitals and 114 fitness and wellbeing centres.
Prisma Access provides scalable protection without the complexity of sizing and deploying firewalls at each location, while Cortex XSOAR automates routine security tasks.
| Pros of Palo Alto Networks Prisma SD-WAN | Cons of Palo Alto SD-WAN | Market Position of Palo Alto SD-WAN |
|---|---|---|
| Palo Alto Networks Prisma SD-WAN (formerly CloudGenix) is recognised for its innovation, particularly in AI operations, granular policy control, and visibility. | One of the drawbacks noted by users is the pricing, especially for licensing large numbers of people. | Recognised as a Leader in Gartner's Magic Quadrant. |
| Palo Alto SD-WAN provides comprehensive visibility into network traffic, allowing easy identification and prioritisation of applications and their traffic. | While Palo Alto SD-WAN is capable in many aspects, it has limited capabilities in certain technical areas, such as TCP and WAN optimisation features. | Recognised for recent and planned innovations across AIOps, visibility, and granular policy control, with potential game-changing capabilities. |
| The platform is noted for its above-average customer experience ratings and a strong understanding of both current and future customer requirements. | The existence of multiple SD-WAN products under the Palo Alto umbrella can lead to market confusion. | Acquired CloudGenix in 2020 to expand and enhance their SD-WAN offerings. |
Is Palo Alto SD-WAN integrating AI?
Palo Alto Networks recognises the importance of Machine Learning (ML) and Artificial Intelligence (AI) in the evolution of SD-WAN, emphasising their role in automating operations and enhancing network performance. By embedding AI and ML into SD-WAN solutions, networks can process massive amounts of data and gain a deeper understanding of network and application performance, leading to a smarter, self-healing, and self-driving network that requires minimal human intervention.
| Product Description | List Price (USD) |
|---|---|
| SD-WAN subscription 5-year prepaid, PA-7080 | $378,000.00 |
| SD-WAN subscription 5-year prepaid for device in an HA pair, PA-7080 | $333,000.00 |
| SD-WAN subscription 5-year prepaid, PA-7050 | $303,000.00 |
| SD-WAN subscription 5-year prepaid for device in an HA pair, PA-7050 | $267,000.00 |
| SD-WAN subscription 3-year prepaid, PA-7080 | $227,000.00 |
| SD-WAN subscription 3-year prepaid for device in an HA pair, PA-7080 | $200,000.00 |
| SD-WAN subscription 5-year prepaid, PA-5280 | $160,000.00 |
| SD-WAN subscription 3-year prepaid renewal, PA-3260 | $17,275.00 |
| SD-WAN subscription 5 year prepaid for device in an HA pair, PA-3250 | $15,400.00 |
| PA-5260 Lab Unit First Year Service Bundle | $15,000.00 |
| SD-WAN subscription 5-year prepaid, PA-3220 | $14,400.00 |
| QuickStart Service for SD-WAN - Hub Deployment | $14,000.00 |
Please note that these prices are subject to change and may vary based on the specific configuration, additional features, and any applicable discounts or promotions.
Barracuda is a North American centric SD-WAN vendor with global presence. The Barracuda core value proposition surrounds their CloudGen Firewall and SecureEdge products. In 2023 and 2024, Barracuda have significantly enhanced their overall SASE features. With approximately 1500 Enterprise customers, the business is known for the cloud-native integration of Microsoft Azure.
Barracuda is best for companies with a focus on cloud vendor integration, especially Microsoft Azure. Alongside native cloud integration, Barracuda also offer significant capabilities across threat protection and cloud based sandboxing to help with malware and zero-hour attacks.
Enhancements also include improvements to reporting, analytics and cloud based-XDR. The CudaLaunch application is designed to secure remote worker connectivity while enforcing policies
If your business is heavily invested in Microsoft Azure, Barracuda is an excellent choice due to their native in-built capability and relationship with Microsoft. This is particularly beneficial for businesses also using Microsoft Office 365 due to route prioritisation.
Hubo improved their network security by implementing Barracuda CloudGen Firewall across 150 stores. Transitioning to an SD-WAN architecture with local internet breakouts, Hubo aimed to enhance connectivity, regulate traffic, and streamline network management across their small IT team.
In collaboration with one of Barracuda's certified partners, Hubo deployed the CloudGen Firewall, managed via the NextGen Control Center platform. Hugo noted how applying a global ruleset allowed efficient settings migration and changes across locations.
The solution provided end-to-end visibility for effective network monitoring, issue troubleshooting, and threat detection. Hubo's IT team is well-prepared to protect against sophisticated cyber threats.
Deploying the Barracuda CloudGen Firewall has transformed Hubo's network security approach, offering granular control, and user-friendly management.
| Pros of Barracuda SD-WAN | Cons of Barracuda SD-WAN | Market Position of Barracuda SD-WAN |
|---|---|---|
| Barracuda SD-WAN incorporates multi-layered, next-generation security features, including cloud-based full emulation sandboxing. | Despite its benefits, Barracuda SD-WAN is noted to be quite expensive. | Recognised as a niche player in Gartner's Magic Quadrant. |
| Barracuda's SD-WAN solution is designed for ease of use, offering out-of-the-box configurations and zero-touch deployment. | While Barracuda SD-WAN is designed to boost network performance, it has shown some limitations in handling link redundancy. | Barracuda's partnership with Microsoft is a unique strength. Leveraging Microsoft Azure and collaborating closely with Microsoft on security solutions indicates a strategic advantage. |
| Barracuda SD-WAN is fully cloud-native to Azure, leveraging Microsoft's Global Network as a WAN backbone. | Barracuda is viewed as primarily a North American centric organisation. |
| Barracuda SD-WAN Product | Description | List Price |
|---|---|---|
| Barracuda CloudGen Firewall F180 | Next-Generation Firewalls for Distributed Enterprises with Advanced Threat Detection | $2,128.00 |
| Barracuda CloudGen Firewall F-Series | Firewalling, IPS, URL filtering, dual antivirus, and application control | $604.20 to $3,040.00 |
Please note that these prices are subject to change and may vary based on the specific configuration, additional features, and any applicable discounts or promotions.
| Aspect |
|
|
|
|
|
|---|---|---|---|---|---|
| SASE Integration | Integrates with Cisco Umbrella for cloud-delivered security services. | Unified SASE services with managed firewall, secure web gateway, and secure remote access. | FortiSASE offers networking and security functionalities in a unified platform. | Seamless integration with Cisco's SASE technologies for a unified network and security platform. | SD-WAN capabilities integrated with WAN backbone and cloud-based security services. |
| SD-WAN Architecture | Abstracted architecture with control and forwarding plane separation across network resources. Includes Cisco vEdge and XE SD-WAN routers. | FlexCore global Layer 2/3 backbone network, offering tiered performance and availability. | Scalable, redundant design with multiple transport options including MPLS and broadband. | Cloud-based management with hub-and-spoke topology, utilising Meraki MX appliances. | Cloud-native software stack minimising edge-compute requirements, global private backbone. |
| Technology Management | Managed via Cisco vManage for centralised control, supporting REST and NETCONF communication. | MyAryaka portal for intuitive, intent-based forwarding rules and policy definition. | Centralised management console for streamlined configuration and management. | Cisco Meraki dashboard for granular control over SD-WAN infrastructure in a cloud-native environment. | Cloud-based application for single-pane-of-glass management of networking and security infrastructure. |
| Core Network | Global scale operation with cloud-based network connectivity management, flexible architecture. | Secure PoPs with integrated WAN acceleration and optimisation, sub-30ms latency to major business areas. | Security-driven network approach, designed for cloud-first and hybrid workforces. | Engineered for cloud-first enterprises, blending SD-WAN functionality with security features. | Global private backbone designed to replace MPLS, optimising cloud application access. |
| Differentiators | Advanced routing capabilities, global support network, integration with Cisco's security portfolio. | Global FlexCore network, sophisticated end-to-end application and network optimisation technology. | Specialised hardware for performance optimisation, self-healing capabilities, application identification. | Cloud-centric management, user-friendly dashboard, integration with Cisco's security portfolio. | Integrated SD-WAN and security solution with a global backbone, cloud-based security services. |
| Aspect |
|
|
|
|
|
|---|---|---|---|---|---|
| SASE Integration | VMware SASE integration for cloud-native network security and connectivity. | Aligns with Gartner’s SASE model, offering tiered security options including next-gen cloud firewalls. | Versa SASE integration for continuous security across multiple access points. | Centralised management of network security policies, traffic segmentation, and built-in encryption. | Integrates next-generation firewall capabilities for comprehensive threat protection. |
| SD-WAN Architecture | Cloud-native architecture supporting edge computing, AI integration for simplified operations. | Flexibility in network connectivity with options for public, private, and 5G wireless access. | Single software platform offering multi-layered security and multi-cloud connectivity. | Cloud and virtual machine setups on universal customer premises equipment. | Combines advanced VPN routing, balancing, and shaping features for optimised performance. |
| Technology Management | Cloud-native platform with AI for IT operations (AIOps) capabilities for proactive network management. | Masergy’s management portal offers a single-pane-of-glass view into network and cloud application delivery. | AI/ML integration for a self-managing, self-healing, and predictive networking solution. | Assists with planning of SD-WAN configuration, including branch and hub communications. | Zero-touch deployment for SecureEdge site devices, requiring no local expertise for setup. |
| Core Network | Part of VMware SASE offering, with expanded PoPs for better cloud connectivity. | Direct connections to the cloud with 100% service availability SLA, secure access to cloud applications. | Carrier-class, flexible, agile, and innovative approach in the NFV market. | Improved reliability, better performance, and enhanced security for IoT integration. | Ensures fast, always-on access to business-critical applications on-premises and in the cloud. |
| Differentiators | Cloud-native design, expansive global PoP network, enhanced performance for voice and video applications. | 24/7 monitoring, software-defined network for enhanced reliability, AI-powered analytics. | Flexibility to scale network resources, multi-tenancy, unified network management. | Prisma Access integration for a unified security posture, AI/ML-driven operations for predictive analytics. | CloudGen WAN integration for optimised cloud application performance, automated threat protection. |
There are several market leaders, which have been recognised by the Gartner 2024 Magic Quadrant. Fortinet, VMware, Cisco, HPE, Versa and Palo Alto are all 2024 SD-WAN leaders.
Yes, in 2024 SD-WAN remains relevant. However, the general view is that SD-WAN will become another component of the Gartner SASE (Secure Access Service Edge) framework.
In 2024, SD-WAN is evolving significantly with trends such as the integration of AI for optimising AI delivery and network management, the rise of SD-WAN as a service within the broader Network-as-a-Service (NaaS) offerings, and the merging of SD-WAN with secure remote access, particularly in the context of Secure Access Service Edge (SASE). In addition, the use of Wireless WAN (WWAN) within SD-WAN, especially leveraging 4G and 5G services, is expected to increase substantially. The advent of quantum computing, securing communications in the post-quantum era is a growing challenge, where Quantum Key Distribution (QKD) are becoming necessary to secure private communication channels.
SD-WAN is regarded as a key technology for future network management due to adaptability and integration with emerging technologies like AI, cloud computing, and 5G. SD-WAN offers the capability to streamline network operations, optimise AI delivery, and support complex business requirements positions SD-WAN as a forward-looking solution.
Next-generation SD-WAN is an advanced evolution of traditional SD-WAN, integrating modern technologies like AI, ML, and automation to offer improved network performance, increased security, and simplified network management.
Robert Sturt, writer for Techtarget and Forbes, has hands-on tested each vendor and service provider. This list of best SD-WAN solutions has been curated based on our experience of SD-WAN capability that matches the needs of most organisations. Within each vendor or provider listing, we have included a link to the hands on test completed by Robert.
With the key features you should consider. And, build a vendor shortlist in less than 60 seconds with our comparison tool.